Welcome to the 17 new people who have joined the crew since last week! If you are new, join us by subscribing here:
If you are new to Telltales, welcome! It’s great to have you here. This newsletter is designed to complement our weekly call/podcast and ultimately enable you develop your ability to think critically and independently about investments. Neither the call/podcast nor this newsletter provide ‘stock tips’ or financial advice. You should always do your own work to determine if an investment is suitable for you. If you are new, please check out the following posts:
Every week I will provide additional data to supplement our weekly Telltales podcast. You can get the podcast on Apple Podcasts, Spotify, or SoundCloud. Follow along with this newsletter to stay up to date!
In last week’s debrief, we discussed the Endpoint Security category of cyber security and dug into customer feedback, growth expectations, and net retention of two leaders in the space, SentinelOne and CrowdStrike. On this week’s episode we discussed Identity and Access Management (and the smaller niche of Privileged Access Management) and the underlying themes, like Zero Trust, that are driving spend in the category. We also discussed two companies that are benefitting from this increased spending - Okta and CyberArk. In today’s debrief we will discuss Identity and Access management and the further subset of that category, Privileged Access Management. Finally, we will dig deeper on the aforementioned companies, Okta and CyberArk.
Zero Trust
Zero trust is an approach to IT system design that centers around a simple concept: devices should not be trusted by default, regardless of if the device is on a trusted network or if it was previously verified.
Modern enterprise environments are a sprawling web of interconnected segments, services, and infrastructure that are hosted both in the cloud and locally. Access to these segments, services, and infrastructure can be local, remote, mobile, server-to-server and IoT (internet of things) driven machine to machine connections. Needless to say, the traditional approach of trusting devices within a particular secured network, or devices connected to it via a VPN, makes less sense in modern enterprise environments.
With Zero Trust, security teams move from assuming identity and integrity based on a set of rules, to explicitly verifying identity and integrity in order to enable access. In order to implement zero trust, the first step is to implement strong identity and access management.
Identity & Access Management
From wikipedia…
Identity & Access Management (IAM) is a framework of policies and technologies to ensure that the right users (in an enterprise) have the appropriate access to technology resources.
Seems simple, right? Implementation, however, can be a nightmare. Historically, this has led to excessively cumbersome provisioning processes and security holes created by incomplete de-provisioning processes. Most importantly, without a strong software solution, these processes and policies cannot scale with the growth in devices and applications needed to operate the modern enterprise.
Identity As A Service (IDaaS) captures a portion of the greater category of companies that provide services in the Identity & Access Management space. The chart below from Forrester Research provides a simplified perspective on the relative merits of some of the players in this space.
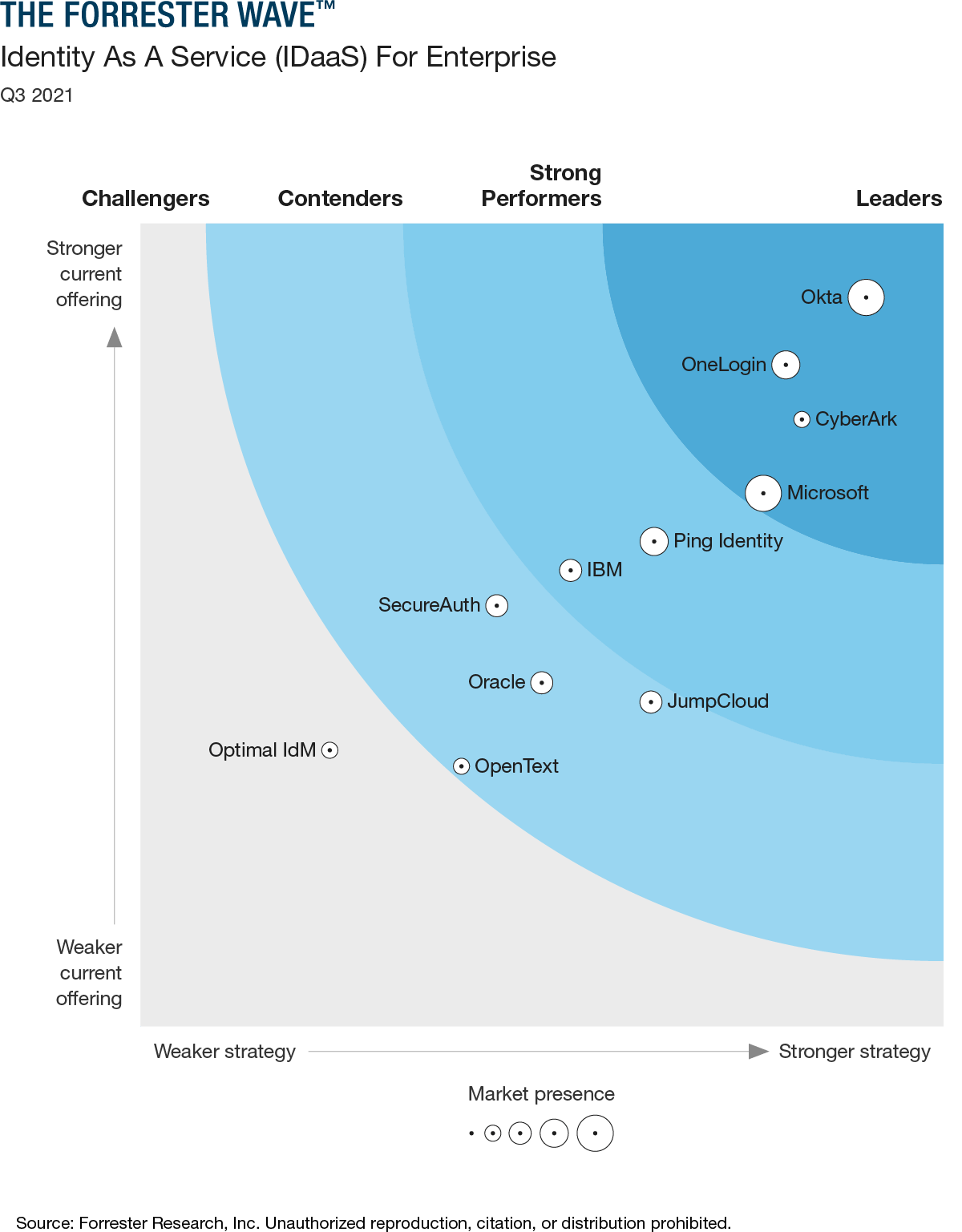
Today we will focus on Okta and CyberArk, but we should also keep Microsoft in mind, as it is one of the supercompounders we discussed in E2132.
Okta (OKTA)
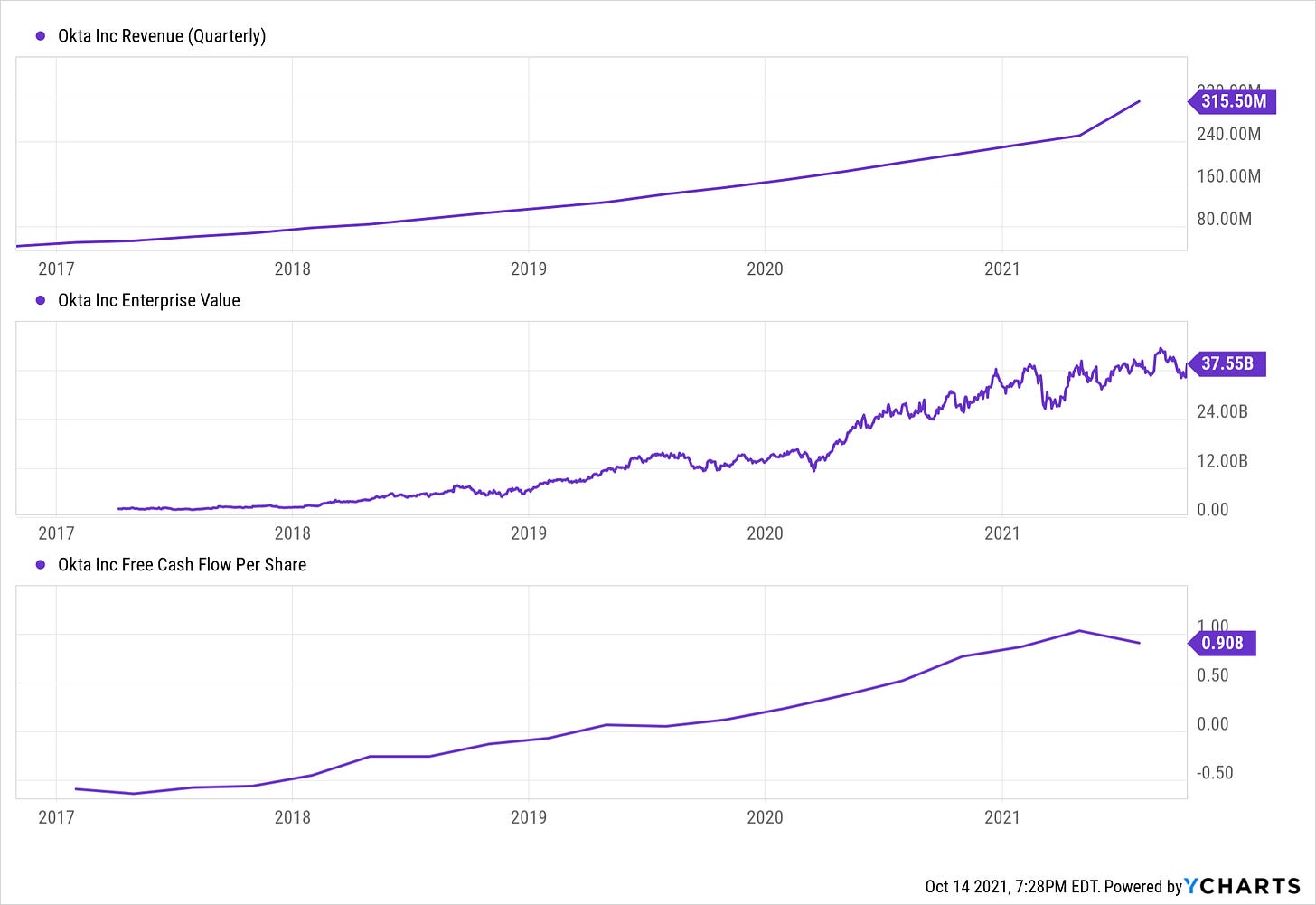
Okta is the leading independent (i.e. not Microsoft) identity management platform for the enterprise. The company publicly listed in April 2017, pricing 11 million shares at $17 per share, above the expected $13-15 per share. Shares jumped more than 35 percent in its first few hours of trading, up to around $23 per share, ultimately valuing the company at $2.096 billion, or approximately 13x FYE January 31, 2017 revenue.
Okta lost $76.3 million in 2016 and $59.1 million in 2015. Sales were $85.9 million in 2016, up 109 percent from $41 million in 2015. Since then, the company has become cashflow positive and is continuing to grow quickly as Zero Trust is adopted by more and more enterprises.
Okta addresses two primary security concerns via its workforce identity and customer identity solutions. The pureplay cybersecurity firm sells products to protect employees, contractors, and partners as well as its customers' end users. Okta's software solutions are cloud-delivered, and its integration network gives customers security protection across a wide variety of applications that are critical to business and government needs. The California-based company went public in 2017 and had over 2,100 employees at the end of the third quarter of fiscal 2020.
Workforce Identity
The slide below shows how Okta sits between all the ‘things’ in a corporate network. What is not shown is the administrative side to the product which makes it easy to both provision and de-provision users. The company is certainly riding the wave of
Customer Identity Management
Customer Identity Management enables 3rd party software builders to build enterprise grade authentication into any app. The developer friendly toolsets Okta has created make it the preferred method for developers to offload customer identity management.
CyberArk
CyberArk Software Ltd. is an Israeli company founded in 1999 with the vision of protecting high-value business data. The company provides a comprehensive solution to secure identities anchored on Privileged Access Management.
CyberArk Software Ltd., a global leader and pioneer of a new layer of IT security solutions that protects organizations from cyber attacks that have made their way inside the network perimeter, announced the closing of its initial public offering of 6,164,000 ordinary shares at a price to the public of $16.00 per share and closed at %29.93 on its first day of trading (an 87% pop) resulting in an enterprise value of just over $800 million USD.
Since the IPO, CyberArk has grown to an enterprise value of $6.7 billion and has become a leading IDM solution. The company’s business model was historically characterized by an enterprise license fee + maintenance fees. In January 2021, the company began transitioning to a recurring revenue model1.
Privileged Access Management (PAM) is a subset of the larger category Identity and Access Management. PAM consists of the cybersecurity strategies and technologies for exerting control over the elevated (“privileged”) access and permissions for users, accounts, processes, and systems across an IT environment2 - often referred to as the ‘keys to the kingdom’.
CyberArk has become the clear leader in PAM, providing a layer of security that protects high level and high value access across an organization. The company has expanded its product offering beyond PAM by acquiring Cybertinel Ltd. in 2017, Vaultive, Ltd. in 2018, and IDaptive Holdings, Inc. in 2020. Cybertinel specialized in cyber threat detection technology and Vaultive is a cloud security provider. IDaptive is an IDaaS provider. The combination of these technologies creates a comprehensive and flexible set of Identity Security capabilities that enables the company to secure access for any identity – human or machine – to help organizations secure critical business assets, protect their distributed workforce and customers, and accelerate business in the cloud.
CyberArk vs Okta
If you’ve been following along the last few weeks (E2137, E2136, E2135…), you’ll remember the following chart and table. These were originally provided by Jamin Ball, author of Clouded Judgement (which I highly recommend reading for updates on SaaS relative valuations). I’ve provided them here again, although I utilized my own data and included some additional companies (like CyberArk) that he does not include, and we utilize different data sources, so our results differ slightly. CyberArk in particular is not a good comp to the rest of these because it is not a SaaS business (though it is transitioning).